With technology comes the ability and temptation to connect every system to a network for enhanced capabilities and control. With each connection, however, the security risk grows. Following a study to quantify and qualify the ever-present, but somewhat nebulous danger, researchers at Pacific Northwest National Laboratory (PNNL) recently released its report “A Cybersecurity Threat Profile for a Connected Lighting System.” Produced for the U.S. Department of Energy (DOE), the study identifies specific cybersecurity threats associated with linking streetlights in an intelligent connected lighting system (CLS) that allows for the remote monitoring of energy use and performance.
DOE estimates connected lighting systems can reduce annual energy usage by 125 TWh by 2035 — if concerns about existing and potential cyber-risks are addressed in product development and deployment. In its study, the PNNL researchers asked, “What are the cybersecurity threats that will impact these systems as formerly banal luminaires transition into intelligent connected devices that collect information about themselves, their surrounding environment, and possibly us?”
Pinpointing problem areas
PNNL researchers conducted and analyzed threat profiles — reports that detail security risks and impact, and controls for mitigation — for six connected streetlighting systems, which offered remote fault detection.
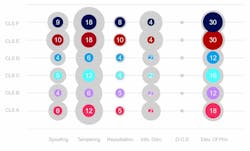
The team modeled on-premise, cloud, and hybrid architectures with different authentication methods using the Microsoft Threat Modeling Tool and categorized them using the Microsoft STRIDE framework: Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, and Elevation of privilege. “Categorizing threats helps identify, organize, and prioritize them,” the researchers wrote.
Findings
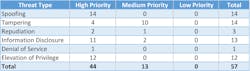
All told, the researchers identified 57 threats, 44 of which they classified as high risk and 13 as medium risk. For high-risk threats, elevation of privileges — in which an unauthorized user gains access to a system — provided the largest attack surface, or number of opportunities within a system through which an attacker can enter. For medium-risk threats, tampering — or the modification of data or code — provided the largest attack surface. All six CLS experienced 77% of the 57 identified threats.
Several threats, such as the high-risk, information disclosure threat, were not specific to the lighting devices but found with the “assets needed to provide connectivity among CLS,” according to the report. Of all threats, 65% were found “within system assets needed to communicate with and control the lighting devices,” such as servers, routers, APIs, and end-user devices.
The researchers identified seven threats (12% of the total) in lighting systems that were specific to their “interactions with an on-premise server, field gateway, and API,” and four threats (7%) specific to interactions with cloud-based systems. Though the quantitative difference is small, the researchers noted that the choice between maintaining on-premise servers and outsourcing to a third party is not to be taken lightly: “Having the proper team and upfront funding in place to operate and maintain, house, and secure the hardware; stay within compliance; and keep a reliable backup option are all considerations. Additional considerations for the end user would include whether utilizing cloud technologies with shared responsibility and access to systems is appropriate for their use case.”
Any connected device brings with it a level of risk. As the number of devices on a network increases, the attack surface will increase. Threats that reside in the lighting devices themselves will scale accordingly as the CLS grows and the network adds luminaires. The researchers demonstrated this relationship by dramatically scaling the number of luminaires by 1,000 and the number of gateways by three for each CLS.
However, the attack surface size does not correlate with threat impact. For example, the researchers noted, “a single uncontrolled [denial-of-service] threat could leave the whole system inoperable. … That is why it is important to approach security from both a quantitative and qualitative standpoint: to be able to prioritize what threats need which controls to obtain the most secure coverage possible.”
Actionable takeaways
With the threats identified and classified, the researchers clarified who is responsible for deploying security controls — manufacturers, third-party suppliers, or the end user? PNNL found that 63% of the threats could be controlled by manufacturers, which could implement defensive techniques, such as encryption and signing the firmware image, to secure their products. Meanwhile, the researchers wrote, “end users are largely responsible for addressing repudiation and elevation of privilege threats.”
Even with manufacturer-deployed controls installed, end users, not knowing the robustness of those controls, could add a complementary backup control to improve their line of defense.
Hybrid systems, comprising devices across multiple vendors (as exemplified by CLS E and CLS F), proffered larger attack surfaces for every STRIDE category. CLS that use Active Directory, a Microsoft-developed authenticator for users and devices, also had a larger attack surface because of the increased number of interactions between systems and between users needing authentication.
Recommendations
Preventing all cyberthreats is improbable, but the researchers acknowledged that “not all threats must be mitigated and perhaps not all threats can be addressed in a cost-effective way; however, without the proper controls in place, an organization will remain at risk.”
The authors outlined several steps that different stakeholders can take to minimize threats. Manufacturers and product developers can:
- Deploy “baked-in technology solutions,” such as encryption and authentication.
- “[R]eview threats involving sourced components,” such as firmware, sensors, and processors, that go into a CLS “to understand how secure supply-chain management or a lack thereof will impact the final product.”
- Adopt or contribute to the development of “standard interoperable protocols for CLS to aid in secure horizontal and vertical communications between IoT assets.”
End users can take the following steps:
- “Conduct a threat profile of their existing or [prospective] CLS, together with any system that might be integrated with the CLS,” and assess whether controls exist to effectively mitigate threats.
- Compare the threat profiles of cloud and on-premise systems or the implementation of a specific vendor solution “to determine which is more suitable for their needs and the abilities of their security team.”
- “Understand which controls they are responsible for implementing and maintaining, and which controls they could, and perhaps should, require from or collaborate on with their vendors or third-party suppliers.”
PNNL recommends that industry regulators and standards and specification developers should define minimum recommended and minimum mandatory (or regulated) controls for connected lighting systems. Its next steps for the industry at-large included strengthening the current body of knowledge to help automate the threat analysis process and characterizing commercially available CLS to determine if manufacturer-implemented controls are in place.
WANDA LAU is editorial director of LEDs Magazine and Smart Buildings Technology. She previously served as executive editor of Architect magazine and worked for a decade in the architecture, engineering, and construction industry.
For up-to-the-minute LED and SSL updates, why not follow us on Twitter? You’ll find curated content and commentary, as well as information on industry events, webcasts, and surveys on our LinkedIn Company Page and our Facebook page.