The rise of Big Data has created a cascade effect across all technologies. From navigation and Bluetooth connectivity in our cars to remotely-controlled smart thermostats in our homes to downloading the latest offers on the fly while grabbing necessities at the local retailer, the Internet of Things (IoT) is no longer emerging but has been steadily marching for some time.
Tapping the ubiquitous lighting hardware, enabled with software and connected to other devices to perform as nodes in an ever-present Internet of Things (IoT) network, building managers, facilities engineers, and other infrastructure personnel can support data-heavy applications like indoor positioning, mobile asset tracking, space optimization, building security, and customer service in the case of retail. How do you ensure that these systems will be secured against entry points and direct attacks?
In our recent webcast, IoT development expert Aniruddha Deodhar, who is principal of connected spaces at Arm Ltd., directly addresses these concerns and offers guiding principles to ensure system integrity, discussing the complexities of connectivity, interoperability of devices and software, and end-to-end security.
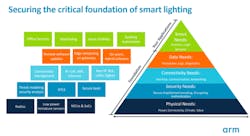
Planners, developers, and engineers can build apps for customers upon the foundation of all the needs in the nearby pyramid graphic. Security is of primary concern; only the safest components should be considered for system implementation and launch.
Security must be built into the core of every device — from the smallest chip — to extend responsibility across the entire value chain before the smart lighting system is ever launched. If even one device has weaknesses, it can be exploited.
Firmware and devices ought to be protected with a sequence of identification, trusted boot instructions, OTA (over-the-air) updates, and authentication processes. All steps must be outlined and implemented properly to lock down gadgets and nodes from threats.
Security can and should start right in the manufacturing process, before your smart lighting baby is ready to be unleashed in a building-wide configuration. What kinds of measures can your electronics providers provision right in the factory? What instructions need to be configured for the on-boarding process after that — who will have ownership of the device and how will it be commissioned? Finally, how will software be updated securely — how will you debug or release patches? And if connectivity fails, what is the backup plan for accessing the device offline in a safe manner?
Deodhar answers these questions and more while attempting to simplify a subject that can appear very daunting at first.
There’s also an informative whitepaper download available in the Resources section once you register and log in for the on-demand webcast. We hope to “see” you at our next webcast!
Security making you squirm? Rest assured, it can be achieved:
Network security can be achieved in commercial smart lighting systems
Learn from the mistakes of others who came before you
Cybersecurity enables the next wave of innovation for smart lighting